Microsoft Azure AD
Testiny can be configured to use Microsoft Azure AD as your identity provider for single sign-on (SSO). Testiny supports configuring both SSO and email login, or restricting logins by requiring SSO logins. This guide explains how to configure the Microsoft Azure AD integration using the OpenID Connect protocol.
This feature is only available in the enterprise plan. Please contact us at [email protected] for more information.
Configuring SSO
To configure SSO with Microsoft Azure AD, you first need to create a web app integration in Microsoft Azure AD and then configure Microsoft Azure AD as the SSO provider in Testiny.
Configuration in Microsoft Azure AD
If you've already created an OAuth client for Testiny in Azure AD, then you can skip this section and continue configuring SSO in Testiny.
-
Log into your Microsoft Azure AD account and go to
Enterprise applicationsas shown in the screenshot below.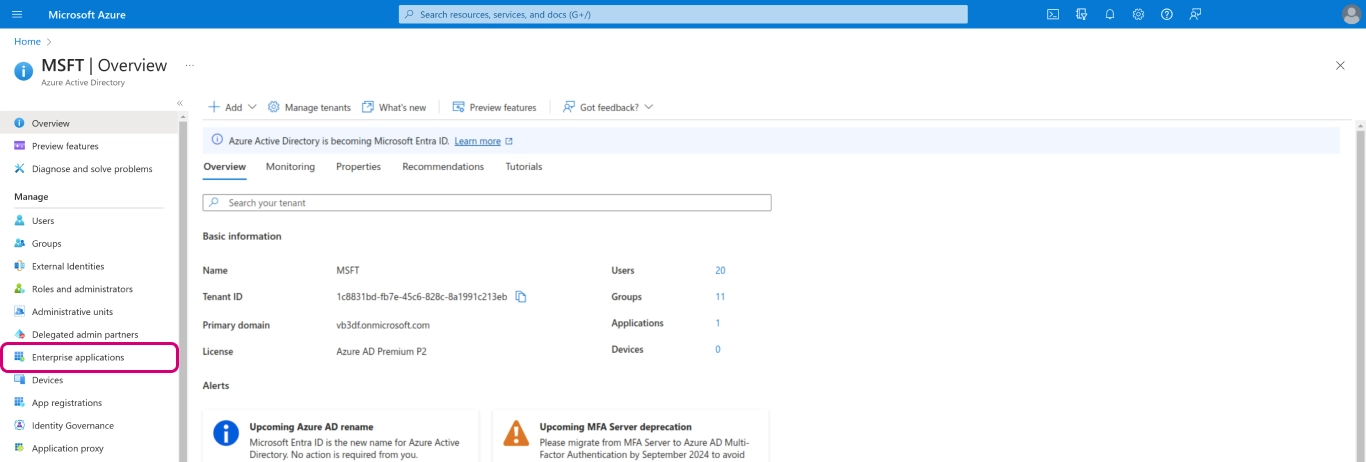
-
Then click on
+ New application.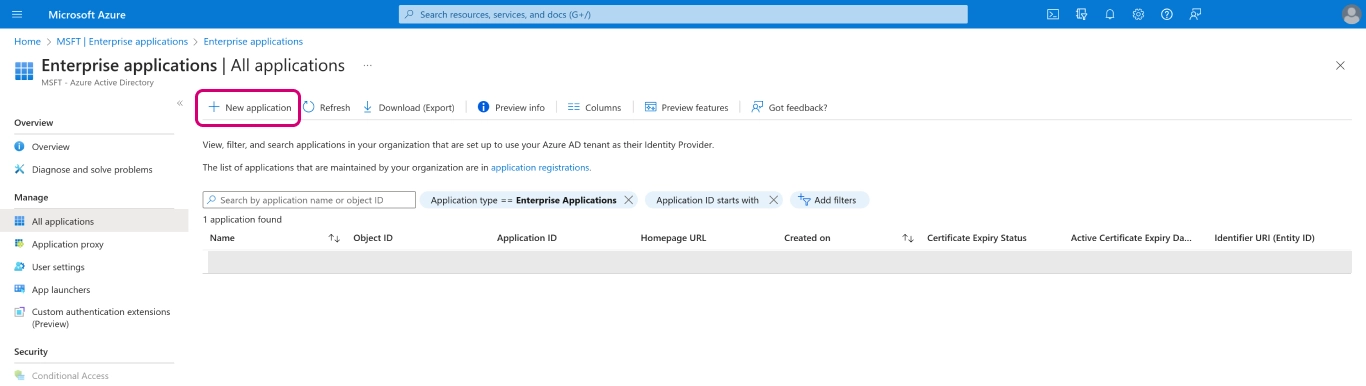
-
Then click on
+ Create your own application(1) and a side panel will open. Enter the name of the app, i.e. 'Testiny' in (2) and select the optionRegister an application to integrate with Azure ADin (3). Finally, clickCreate(4).
-
Then click
Register.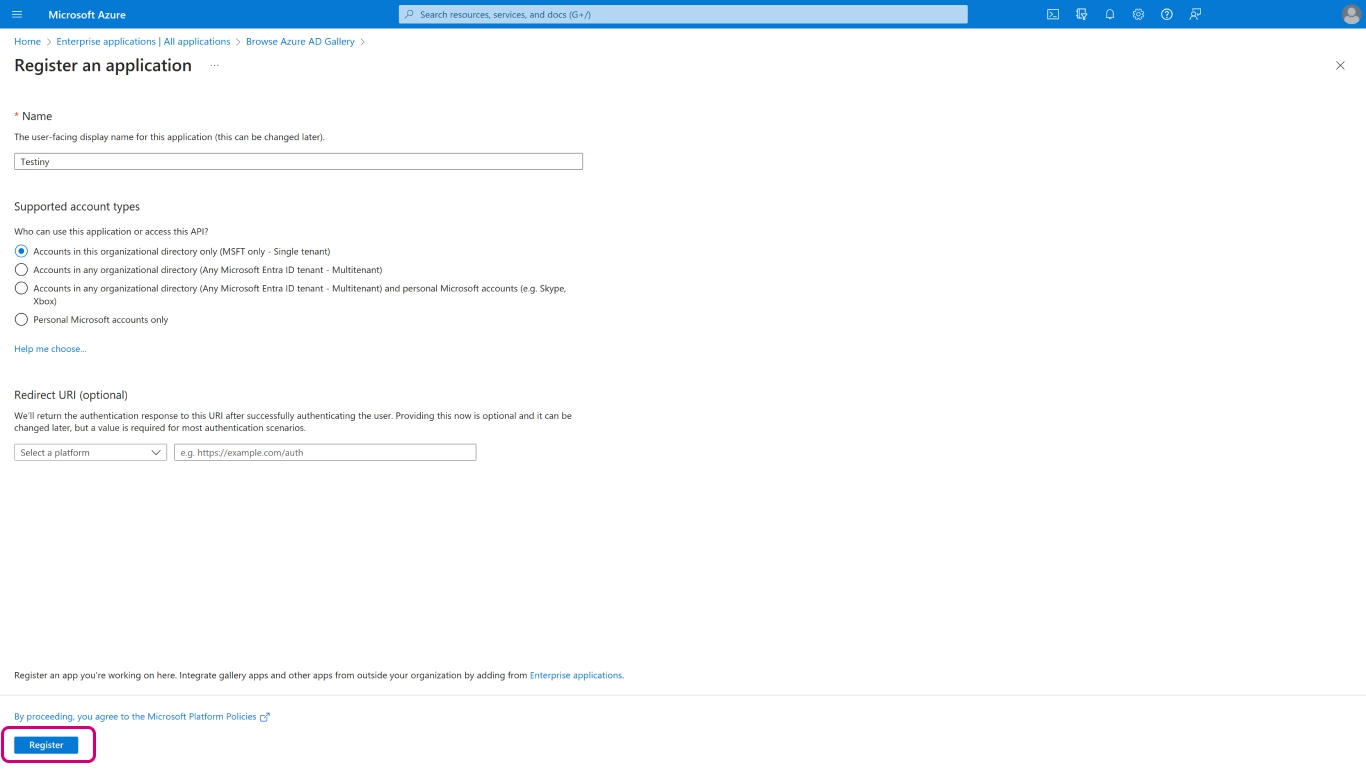
-
In the newly created application, go to `Properties". Here you can optionally upload the Testiny logo. You can download the Testiny logo here.
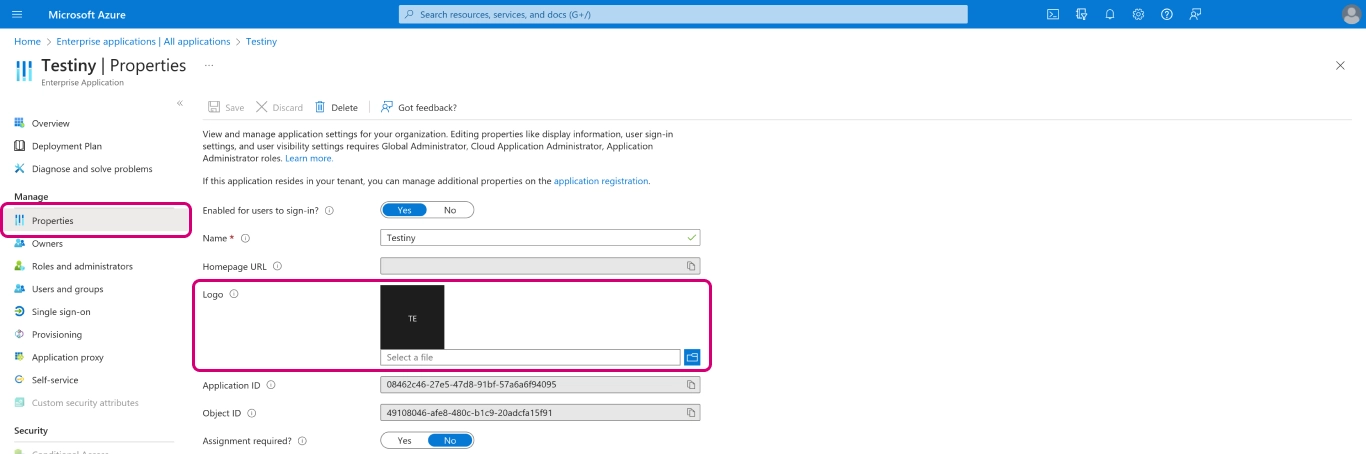
-
Then go to
Single sign-onand click onGo to application.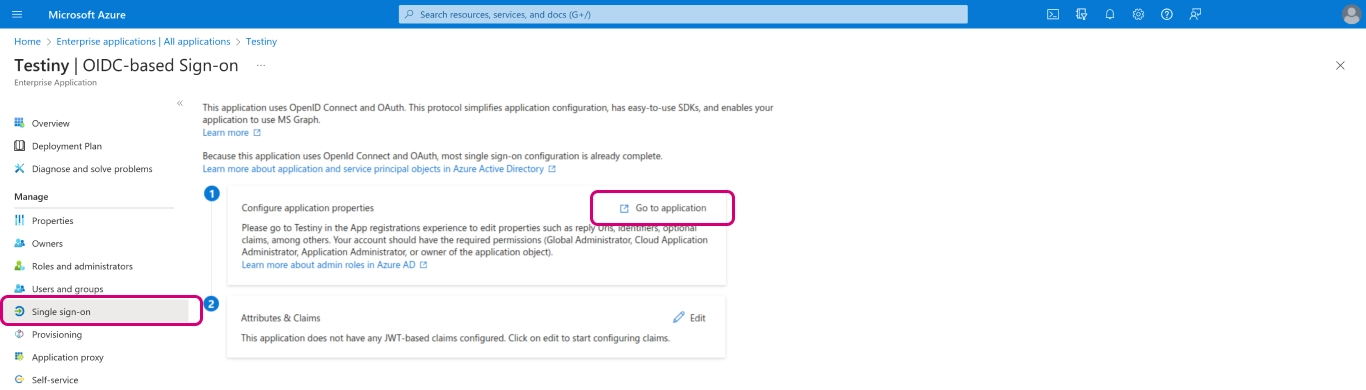
-
In this overview, please note that you can find the application/client ID (1) and the directory/tenant ID. You'll need these values later on for the configuration in Testiny.
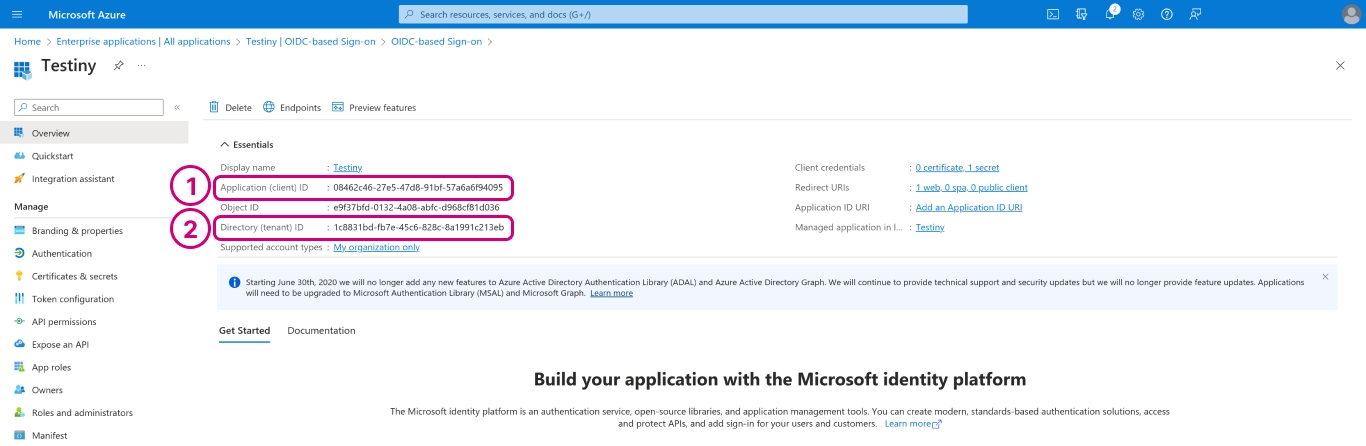
-
To configure the app integration, continue to
Authentication(1), click on+ Add platform(2) and in (3) selectWeb.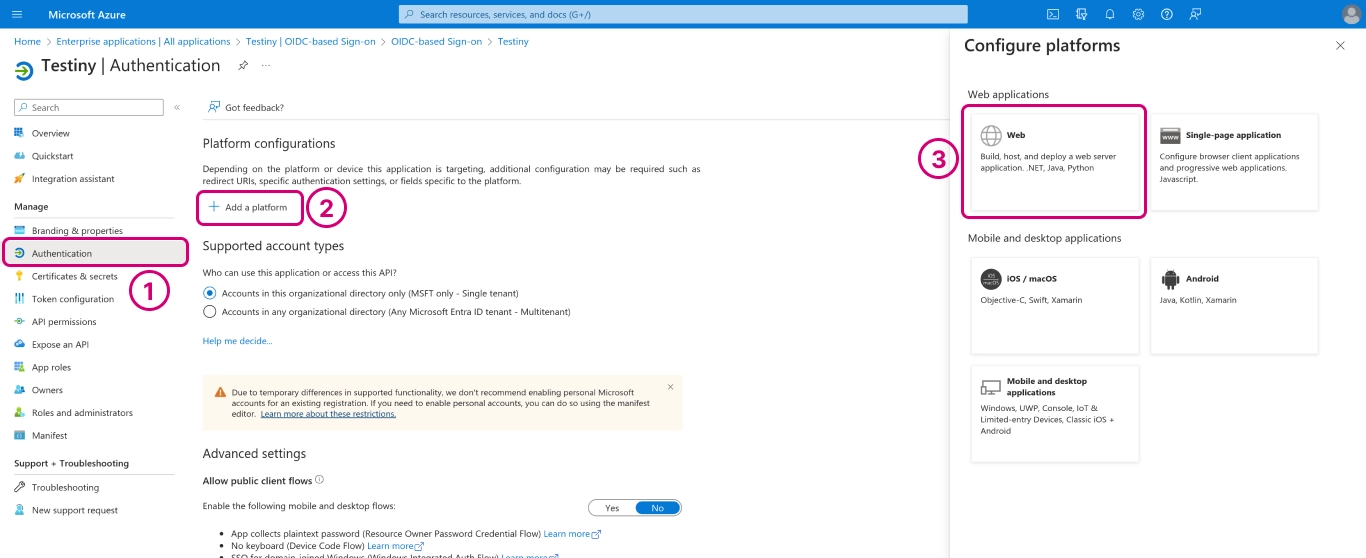
-
Now add the following URL as an allowed redirect URI (1):
https://app.testiny.io/api/v1/oauth/redirect
In (2), add the following URL as an allowed logout URL:
https://app.testiny.io/api/v1/auth/logout
In (3), check the box forID tokens. Then clickConfigure(4) to save these settings.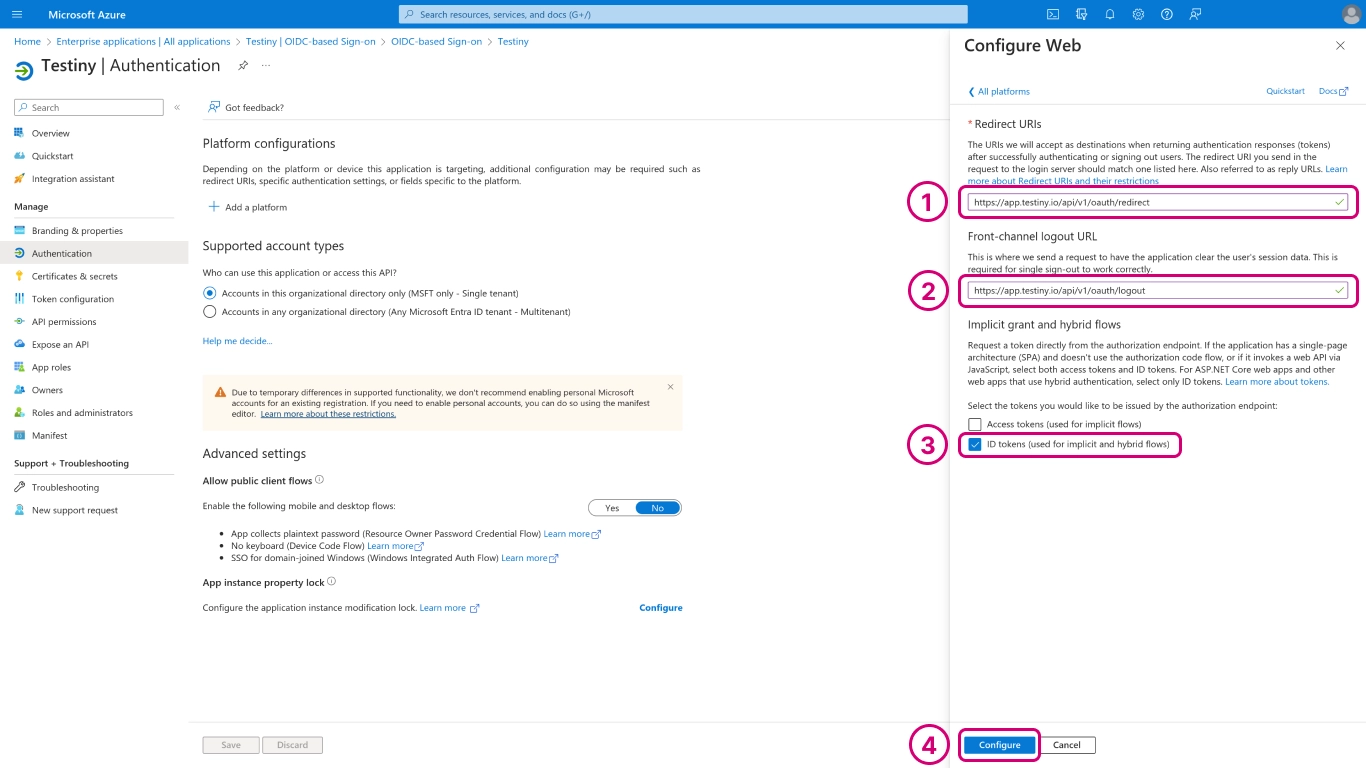
-
Then go to
Certificates & Secrets(1), click on+ New client secretand add a description, e.g. 'Testiny' in (3). You can also change the expiration of the secret or leave the default setting. Then clickAdd(4).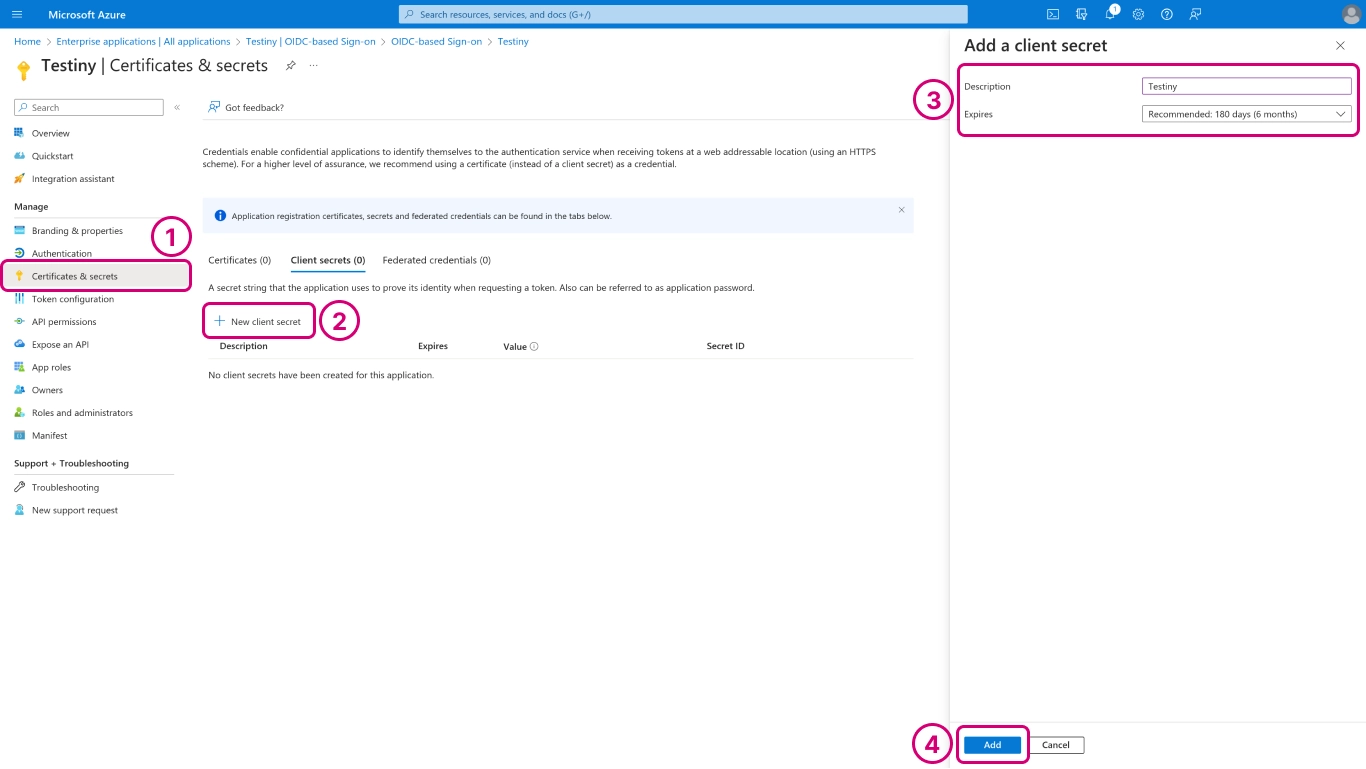
-
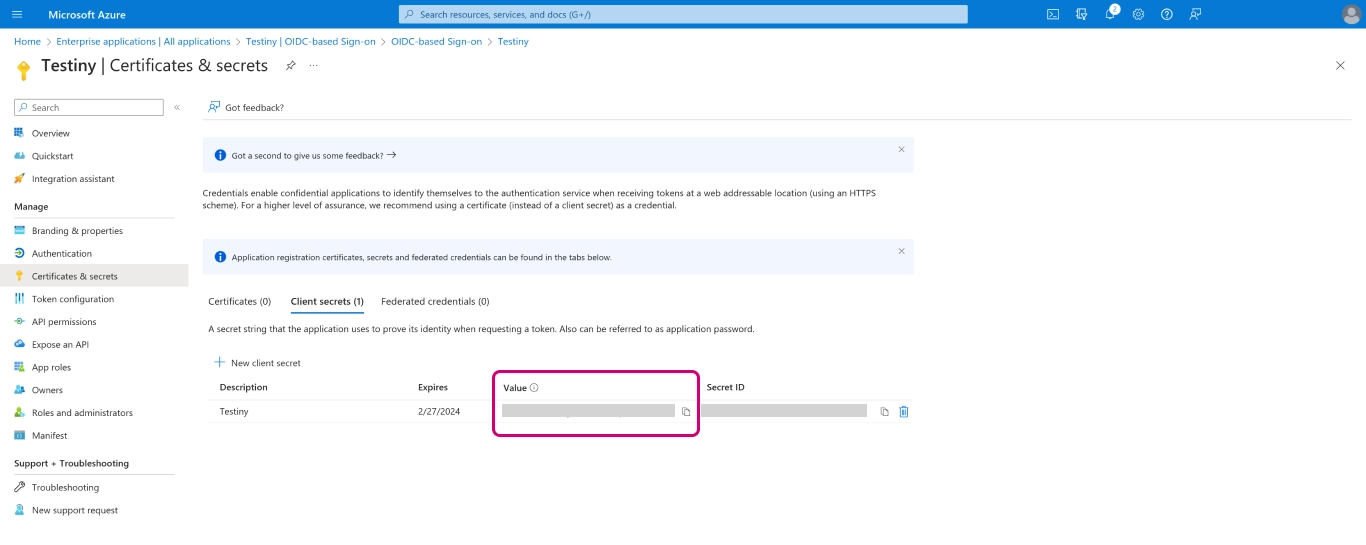
Please note and copy the value of the secret. You'll need it in the next step when configuring SSO in Testiny.
Configuration in Testiny
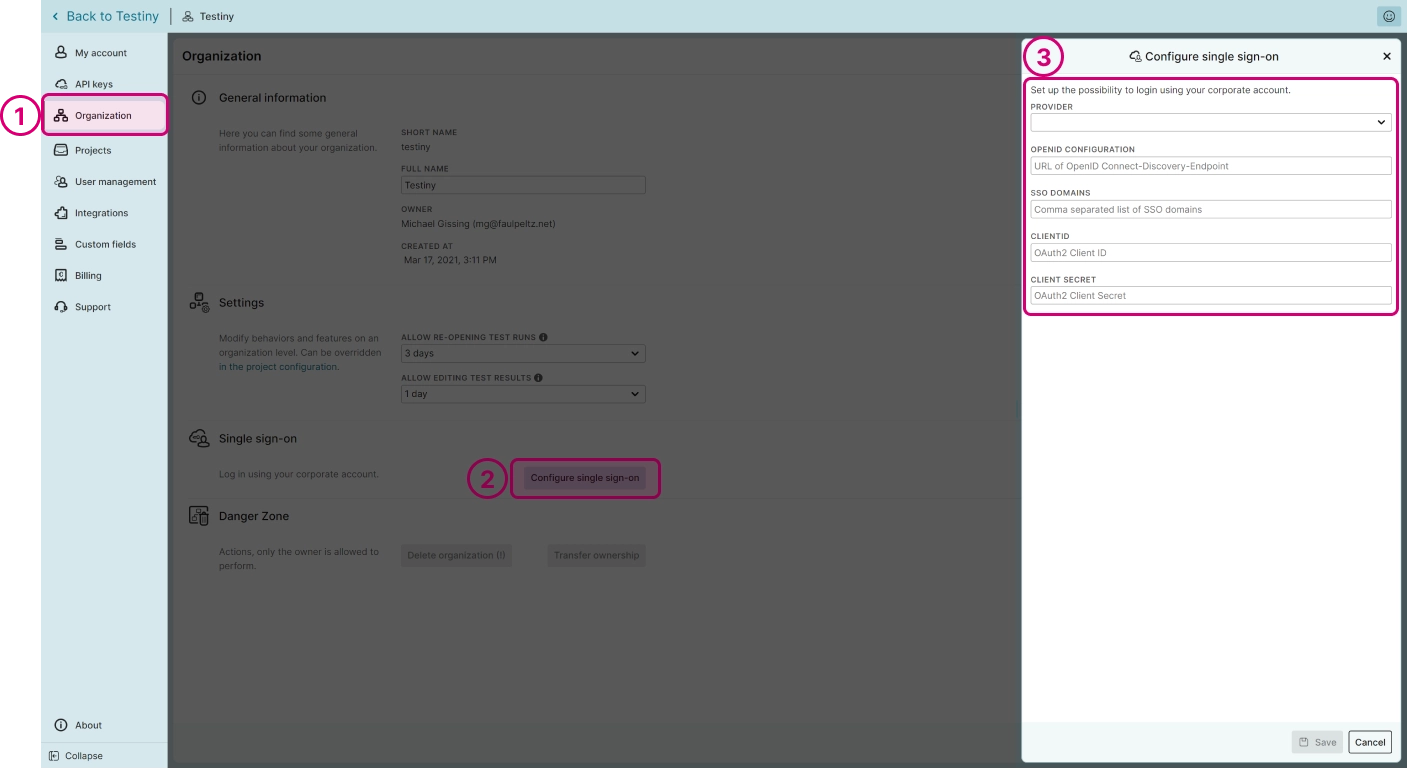
To configure Microsoft Azure AD as your SSO provider, you need to have admin rights in Testiny. In Testiny, go to the settings and select Organization (1), as shown in the screenshot below. Click on 'Configure single sign-on' (2). A side panel (3) opens where you need to define the following options:
- Provider — Choose 'Microsoft Azure AD' from the list.
- OpenID Configuration — Specify the URL to the OpenID Connect metadata. In Microsoft Azure AD, the URL should look like the following example:
https://login.microsoftonline.com/((tenantId:a))/v2.0/.well-known/openid-configuration
Replace tenantId:a with the value from your Microsoft Azure AD account. You can find this value as shown in step 7 in the section above on how to configure an app client in Azure AD or see the Azure AD documentation. - SSO Domains — Enter the domains that will be able to use single sign-on.
3.1 If you have already invited users from these domains to your Testiny organization, an option will show up to change the login type of these users. By default, the users' login type will be set to "SSO allowed". - Client ID — Enter the client ID of the client created in Microsoft Azure AD. You can copy the ID from your app client as described above in step 7 in the section on how to configure an app client in Azure AD.
- Client Secret — Enter the client secret of the client created in Microsoft Azure AD. You can copy the secret value from your app client as described above in the last step in the section on how to configure an app client in Azure AD.
- Click on "Save". Once SSO is successfully configured, you can invite SSO users to your organization or update existing users to use SSO login in the user management settings.
To invite users to your organization, navigate to Settings > User management and click the "Invite" button in the top left corner. A side panel will appear, where you can choose whether the SSO login is allowed, required or disabled:
- allowed — the user can log in via SSO, but can also create a password in Testiny and use the email login
- required — the user must log in via SSO
- disabled — the user cannot log in via SSO, only with email login
Then, enter the email address of the user to be added and optionally the first and last name. In the "Role" drop-down, you can adjust the user’s permissions. Learn more about the user management in Testiny.
Logging into Testiny
When SSO is configured in your Testiny organization and the user is invited as an SSO user, they can simply log in to Testiny on the login page. When SSO is required, the user can only log in with SSO. If SSO is allowed but not required, the user might also log in via email and password.
Please note that the owner of the organization in Testiny cannot be restricted to require SSO login so that the owner can always log in with email & password.
Testiny uses the Microsoft Azure AD email address claim as the username. This means that you must use your email address as your username to login to Testiny. You cannot login using your User Principal Name (UPN).
Disabling SSO
To disable SSO, go to Settings > Organization and click the next to the configured provider. A dialog will be shown to see which users are affected and cannot log in via SSO anymore. After confirming, SSO is disabled and you continue using email/password login or set up a new SSO provider.
Changing your SSO provider
If you want to modify your SSO configuration or change to another SSO provider, simply click the "Configure sinlge sign-on" button to open the configuration side panel. You can change the SSO provider and set up a new SSO configuration, or add new SSO domains to your current configuration. If you remove an SSO domain, single sign-on may be deactivated for users in this SSO domain.